Simply Accessing the Unprotected Admin or Administrator account.
How this hack works ? When we install windows XP on our system we usually rename the username as our name or some other keyword. But windows always creates the administrator account whenever we set up windows XP. So when you create your user account during install , windows creates two accounts that is one is your username account and other is Administrator account. But the main thing is that you will only see the account with your username and the Administrator account is hidden but its there and you can easily access that using the following steps:
Step1: Start your computer.
Step2: Now let it start until the windows user's username appears as shown in snapshot below...
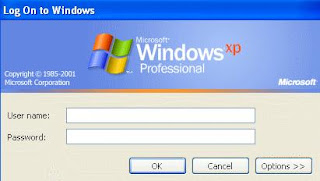
Step3: As This Window Appears Press Ctrl+Alt +Delete (2 times).. Now the Windows like shown below appears..
Step4: Now as shown above Enter the Administrator on the Username box and press enter... Now you will be login in the admin account can easily rest the password...
For Resetting password you can follow two Procedures..
Procedure 1: Goto Start --> Control Panel --> User Accounts.. Now select the account whose password u want to reset.
Procedure 2 : Follow the Next method i.e hacking password through Net User Command.
Note: Hack 1 will only work if Administrator(default) is unsecure.
Enjoy!!!